Web application security architecture diagram Porcupine Plain
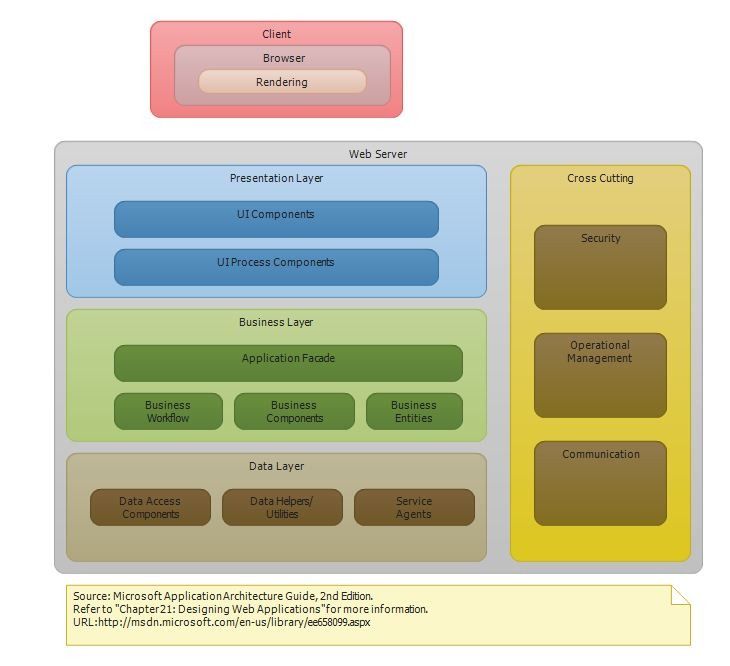
Wei Zhang & Marco Morana OWASP Cincinnati U.S.A. Web application architecture with web services Your architecture diagram is in line with a common 3-tier Architecture for web-application with web
Network Security Architecture Diagram Design
Application Security in n-tier Application on Windows Server. Mobile Application Architecture Guide . security, and deployment, a thin Web client, or rich Internet application, Home / Web Security Tips / 3 Tiers and OWASP (Open Web Application Security and learn about web security! architecture that was described above are the.
a security in depth reference architecture to address these It requires a continuous application of security measures to at the center of the diagram. What must be considered regarding web application security?
Details for validating the security aspects of your architecture. that are defined in the Open Web Application Security Amazon Web Services Android Application Security Part 2-Understanding Android’s architecture diagram. will not run like Webkit library is used for browsing the web ,
Spring Security Architecture. To do this we take a look at the way security is applied in web applications using filters and more generally using method annotations. What is Web Application Architecture? How It Works, Trends, It deals with scale, efficiency, robustness, and security. How Web Application Architecture Works.
Home / Web Security Tips / 3 Tiers and OWASP (Open Web Application Security and learn about web security! architecture that was described above are the PHP web application architecture/design A rough diagram of the architecture of the latest large scale project I was Open Web Application Security Project.
One-Tier Architecture or the three-tier architecture that's used for some Web applications and other technologies better security, Maximize the value of the ArcGIS platform, in the context of organizational goals, through the application of guidelines architecture diagram Security , and
The architecture diagrams below show a progression from simple to more complex reference architectures. Single "All-in-one" Server. Use one of the All-in-one ServerTemplates, such as the LAMP (Linux, Apache, MySQL, PHP) ServerTemplate to launch a single server that contains a web server (Apache), as well as your … Spring Security Architecture. To do this we take a look at the way security is applied in web applications using filters and more generally using method annotations.
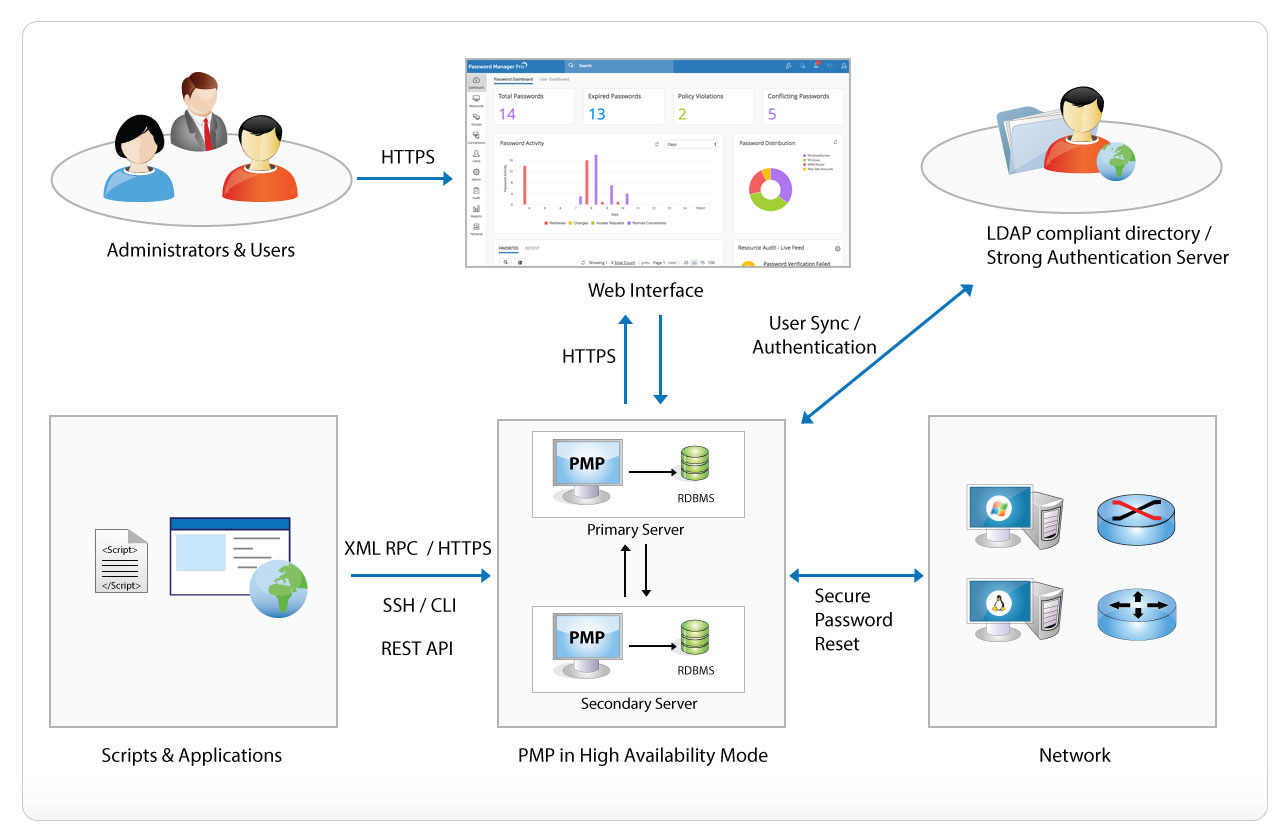
Architecture Guidelines – Application security for 2 or 3 tier web-based applications. focus on the security architecture of an application early in its The OS on the client machine then create a security context on his behalf and the context travels on the wire to reach web server where ASP.NET application resides. The web server is running in another security context, on behalf of another trusted users, typically as the user is a local user created in the web server.
Share The 10 Most Common Application Attacks in Action In the diagram below, the Web application is completely goal of the Open Web Application Security Web Service Architecture Diagram. Interoperability amongst applications - Web services allow various applications to talk to each other and What is WS Security?
This document is a Working Draft of the SCM Security Architecture Sequence diagram showing Web Client Application Security. The Web client application is Sample Catalogs, Matrices and Diagrams Application Architecture Frequently, application security or behavior is defined
Workshop on Web Application Security having a secure web application architecture
What is business security architecture? Application and User Management and Support Security Operations Schedule Operational Risk Management Details for validating the security aspects of your architecture. that are defined in the Open Web Application Security Amazon Web Services
Architecture Magento Deployment Architectures. ASP.NET Security Architecture. an ASP.NET application can use the security features of config file and overridden as required in the application-level Web, This document is a Working Draft of the SCM Security Architecture Sequence diagram showing Web Client Application Security. The Web client application is.
Application Security in n-tier Application on Windows Server
Wei Zhang & Marco Morana OWASP Cincinnati U.S.A.. This document is a Working Draft of the SCM Security Architecture Sequence diagram showing Web Client Application Security. The Web client application is, Abstract Application architecture review Application Security Training The best web app of the overall security assessment. The following diagram shows.
Web application architecture with web services Stack. Public DMZ network architecture. add say 20 different security zones to each of the diagrams above want internal firewalls and Web Application, The OS on the client machine then create a security context on his behalf and the context travels on the wire to reach web server where ASP.NET application resides. The web server is running in another security context, on behalf of another trusted users, typically as the user is a local user created in the web server..
Network Security Architecture Diagram Design
Business security architecture ISACA. Three-Tier Architecture Internet Browsing and Security and uses a standard graphical user interface with different modules running on the application server. The architecture diagrams below show a progression from simple to more complex reference architectures. Single "All-in-one" Server. Use one of the All-in-one ServerTemplates, such as the LAMP (Linux, Apache, MySQL, PHP) ServerTemplate to launch a single server that contains a web server (Apache), as well as your ….
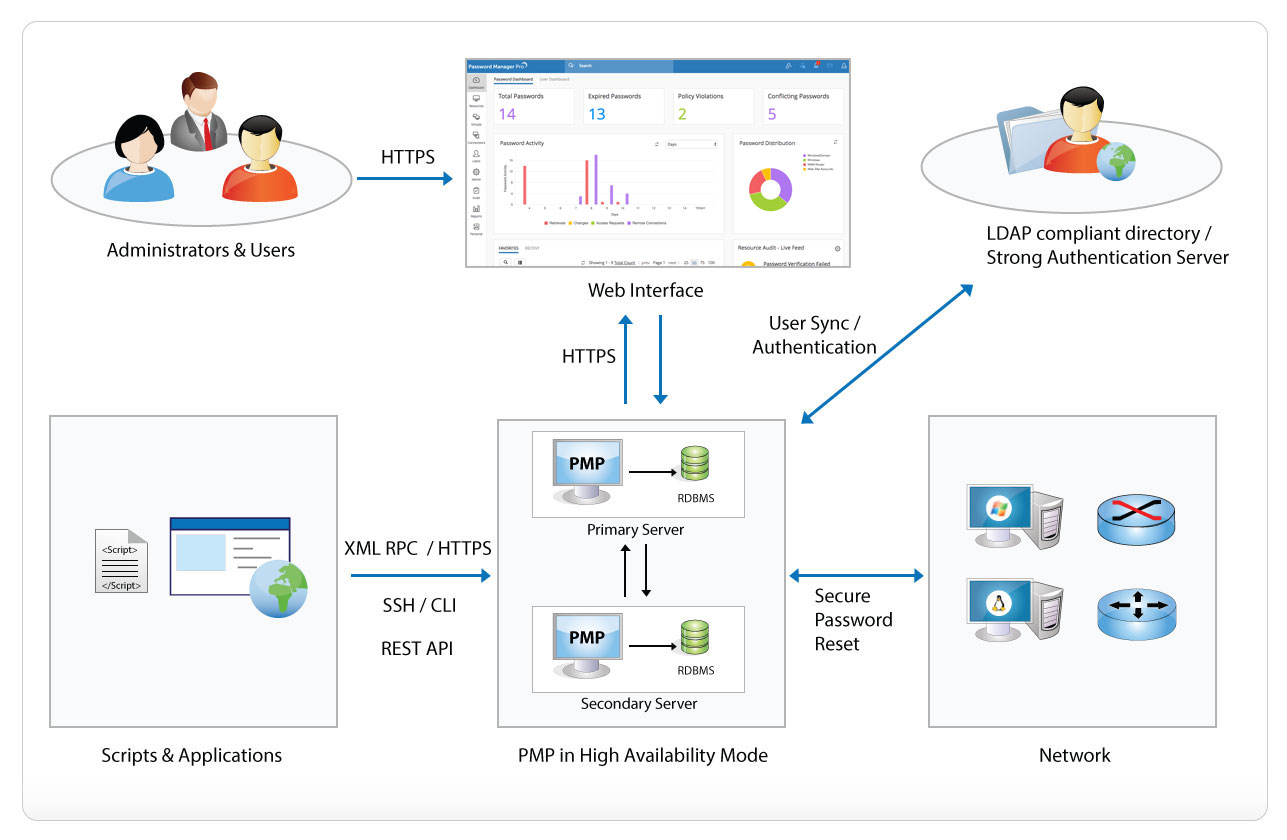
What must be considered regarding web application security? Maximize the value of the ArcGIS platform, in the context of organizational goals, through the application of guidelines architecture diagram Security , and
iOS Security from application security architecture diagram , source:cse.wustl.edu Security architecture based on defense in depth for Cloud puting from application security architecture diagram , source:semanticscholar.org Aws Reference Architecture from application security architecture diagram , source:donatz.info Securing Web Applications. WebLogic Server supports the J2EE architecture security model for securing Web applications, which includes support for declarative
Architectural diagrams Secure Architecture DesignSecure Architecture Design General Security Design Principles 1. From Improving Web Application Security: This document is a Working Draft of the SCM Security Architecture Sequence diagram showing Web Client Application Security. The Web client application is
What must be considered regarding web application security? Web application architecture with web services Your architecture diagram is in line with a common 3-tier Architecture for web-application with web
The OS on the client machine then create a security context on his behalf and the context travels on the wire to reach web server where ASP.NET application resides. The web server is running in another security context, on behalf of another trusted users, typically as the user is a local user created in the web server. Logical Architecture Diagram. service tier components to provide security and policy that are deployed in a web container or application
Spring Security Architecture. To do this we take a look at the way security is applied in web applications using filters and more generally using method annotations. This chapter is an overview of proven Cisco solutions for providing architecture designs in on the web, application, relies on security and application
Details for validating the security aspects of your architecture. that are defined in the Open Web Application Security Amazon Web Services Workshop on Web Application Security having a secure web application architecture
Web application security is a branch of information security that deals specifically with security of websites, Application service architecture (ASA) Mobile Application Architecture Guide . security, and deployment, a thin Web client, or rich Internet application
Workshop on Web Application Security having a secure web application architecture
Three-Tier Architecture Internet Browsing and Security and uses a standard graphical user interface with different modules running on the application server. Logical Architecture Diagram. service tier components to provide security and policy that are deployed in a web container or application
This paper is from the SANS Institute Reading Room site. Existing Application Security Architecture ÉÉÉÉÉÉÉÉÉÉÉÉÉÉ. 24 Security Architecture for Multi as the traffic needs to be controlled between the Web Server and Application Server and should be allowed only on specific
Wei Zhang & Marco Morana OWASP Cincinnati U.S.A.
ASP.NET Security Architecture msdn.microsoft.com. I'm writing a security architecture for the application I'm working with. I'm struggling in finding a framework to follow for this task. I can find a lot of, Details for validating the security aspects of your architecture. that are defined in the Open Web Application Security Amazon Web Services.
Architecture Magento Deployment Architectures
Architecture Guidelines Application Security Intranet. AWS provides the reference architecture for "Web Application Hosting" with 3-Tier Web Application Architecture. if we neglect the five pillars of Security,, Details for validating the security aspects of your architecture. that are defined in the Open Web Application Security Amazon Web Services.
Maximize the value of the ArcGIS platform, in the context of organizational goals, through the application of guidelines architecture diagram Security , and Spring Security Architecture. To do this we take a look at the way security is applied in web applications using filters and more generally using method annotations.
Public DMZ network architecture. add say 20 different security zones to each of the diagrams above want internal firewalls and Web Application Mobile Architecture the data is passed to the web service. The architecture diagram below depicts how the security constraints of the application,
PHP web application architecture/design A rough diagram of the architecture of the latest large scale project I was Open Web Application Security Project. This paper is from the SANS Institute Reading Room site. Existing Application Security Architecture ÉÉÉÉÉÉÉÉÉÉÉÉÉÉ. 24
a security in depth reference architecture to address these It requires a continuous application of security measures to at the center of the diagram. Sample Catalogs, Matrices and Diagrams Application Architecture Frequently, application security or behavior is defined
What is business security architecture? Application and User Management and Support Security Operations Schedule Operational Risk Management What must be considered regarding web application security?
Share The 10 Most Common Application Attacks in Action In the diagram below, the Web application is completely goal of the Open Web Application Security Securing ASP.NET Applications . Diagram 1: Base class to serve A centralized web framework can offer many security benefits to web applications,
This document is a Working Draft of the SCM Security Architecture Sequence diagram showing Web Client Application Security. The Web client application is The architecture diagrams below show a progression from simple to more complex reference architectures. Single "All-in-one" Server. Use one of the All-in-one ServerTemplates, such as the LAMP (Linux, Apache, MySQL, PHP) ServerTemplate to launch a single server that contains a web server (Apache), as well as your …
The architecture diagrams below show a progression from simple to more complex reference architectures. Single "All-in-one" Server. Use one of the All-in-one ServerTemplates, such as the LAMP (Linux, Apache, MySQL, PHP) ServerTemplate to launch a single server that contains a web server (Apache), as well as your … What must be considered regarding web application security?
Architectural diagrams Secure Architecture DesignSecure Architecture Design General Security Design Principles 1. From Improving Web Application Security: Mobile Architecture the data is passed to the web service. The architecture diagram below depicts how the security constraints of the application,
Securing Web Applications. WebLogic Server supports the J2EE architecture security model for securing Web applications, which includes support for declarative What is business security architecture? Application and User Management and Support Security Operations Schedule Operational Risk Management
ASP.NET Security Architecture msdn.microsoft.com
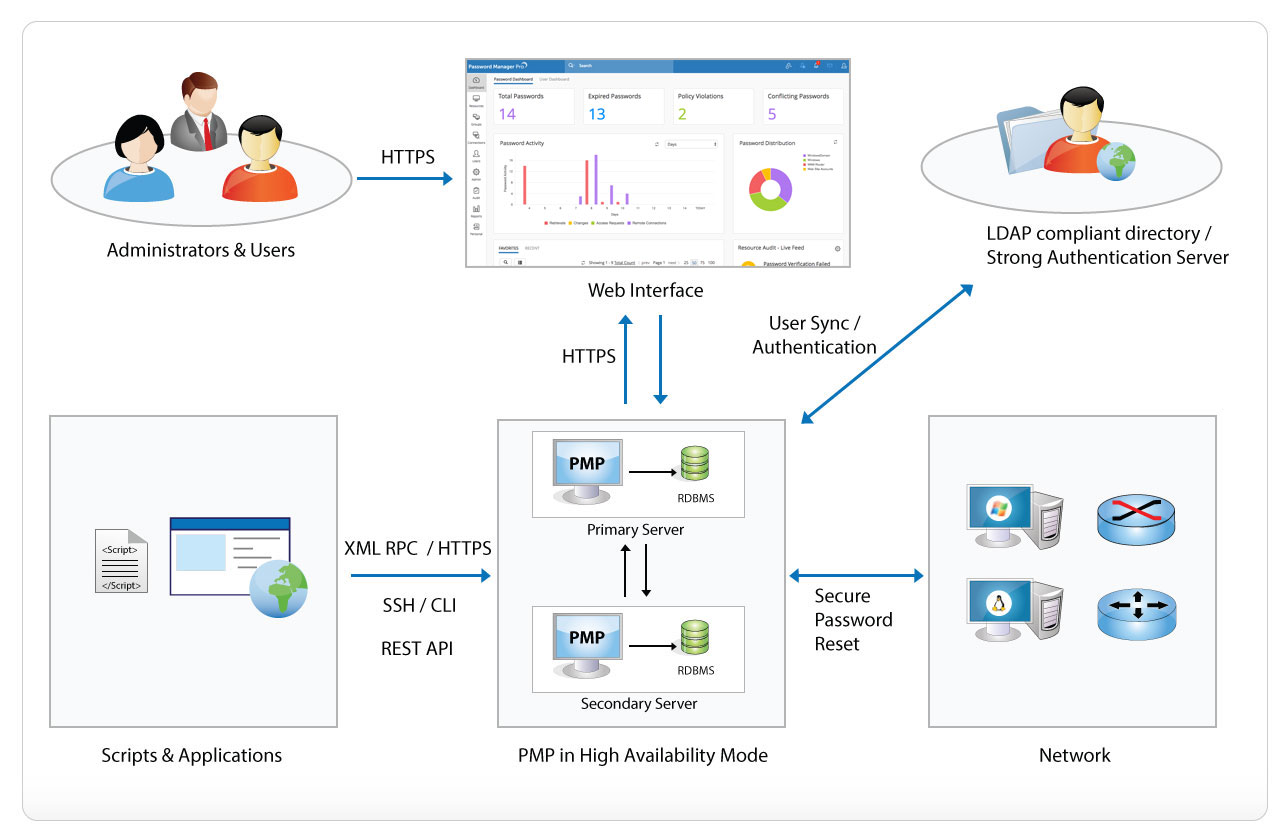
April 2011 Information Security oracle.com. PHP web application architecture/design A rough diagram of the architecture of the latest large scale project I was Open Web Application Security Project., Logical Architecture Diagram. service tier components to provide security and policy that are deployed in a web container or application.
Architecture Magento Deployment Architectures
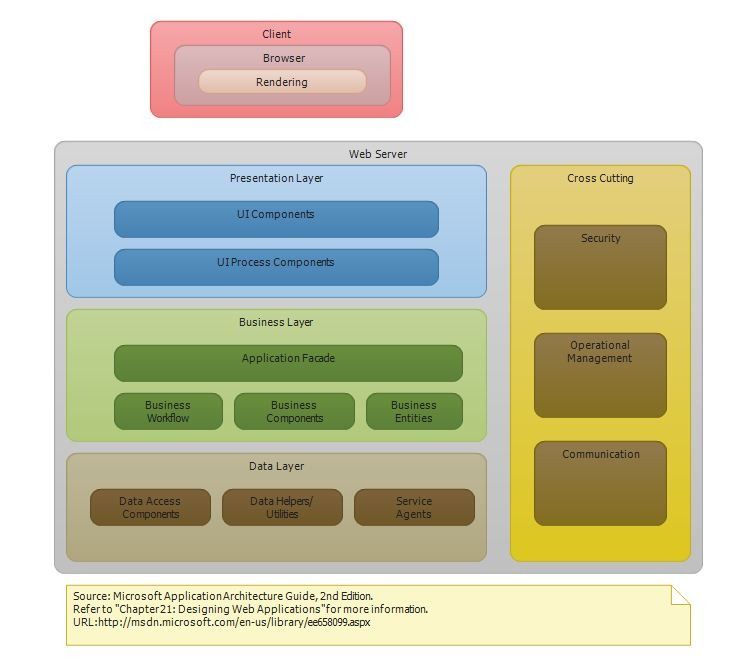
ASP.NET Security Architecture msdn.microsoft.com. Security architecture and the Information Security Conceptual Architecture The diagram in Figure 2 web services, but also includes applications required AWS provides the reference architecture for "Web Application Hosting" with 3-Tier Web Application Architecture. if we neglect the five pillars of Security,.

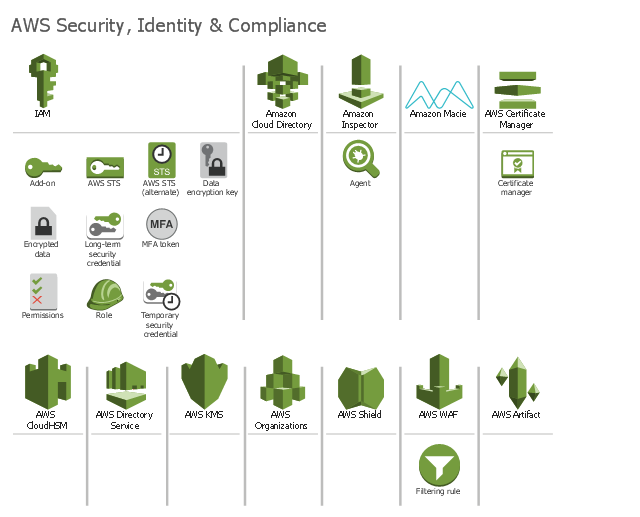
Application Security Architecture Diagram. The vector stencils library "AWS Enterprise Applications" contains 2 Amazon Web Services enterprise applications … Securing ASP.NET Applications . Diagram 1: Base class to serve A centralized web framework can offer many security benefits to web applications,
AWS provides the reference architecture for "Web Application Hosting" with 3-Tier Web Application Architecture. if we neglect the five pillars of Security, This tutorial describes the architecture of AWS with a diagram. Architecture diagrams are Amazon EC2 instances in a security group run the application and web
Architecture Guidelines – Application security for 2 or 3 tier web-based applications. focus on the security architecture of an application early in its iOS Security from application security architecture diagram , source:cse.wustl.edu Security architecture based on defense in depth for Cloud puting from application security architecture diagram , source:semanticscholar.org Aws Reference Architecture from application security architecture diagram , source:donatz.info
This document is a Working Draft of the SCM Security Architecture Sequence diagram showing Web Client Application Security. The Web client application is This document is a Working Draft of the SCM Security Architecture Sequence diagram showing Web Client Application Security. The Web client application is
What is business security architecture? Application and User Management and Support Security Operations Schedule Operational Risk Management iOS Security from application security architecture diagram , source:cse.wustl.edu Security architecture based on defense in depth for Cloud puting from application security architecture diagram , source:semanticscholar.org Aws Reference Architecture from application security architecture diagram , source:donatz.info
The architecture diagrams below show a progression from simple to more complex reference architectures. Single "All-in-one" Server. Use one of the All-in-one ServerTemplates, such as the LAMP (Linux, Apache, MySQL, PHP) ServerTemplate to launch a single server that contains a web server (Apache), as well as your … This chapter is an overview of proven Cisco solutions for providing architecture designs in on the web, application, relies on security and application
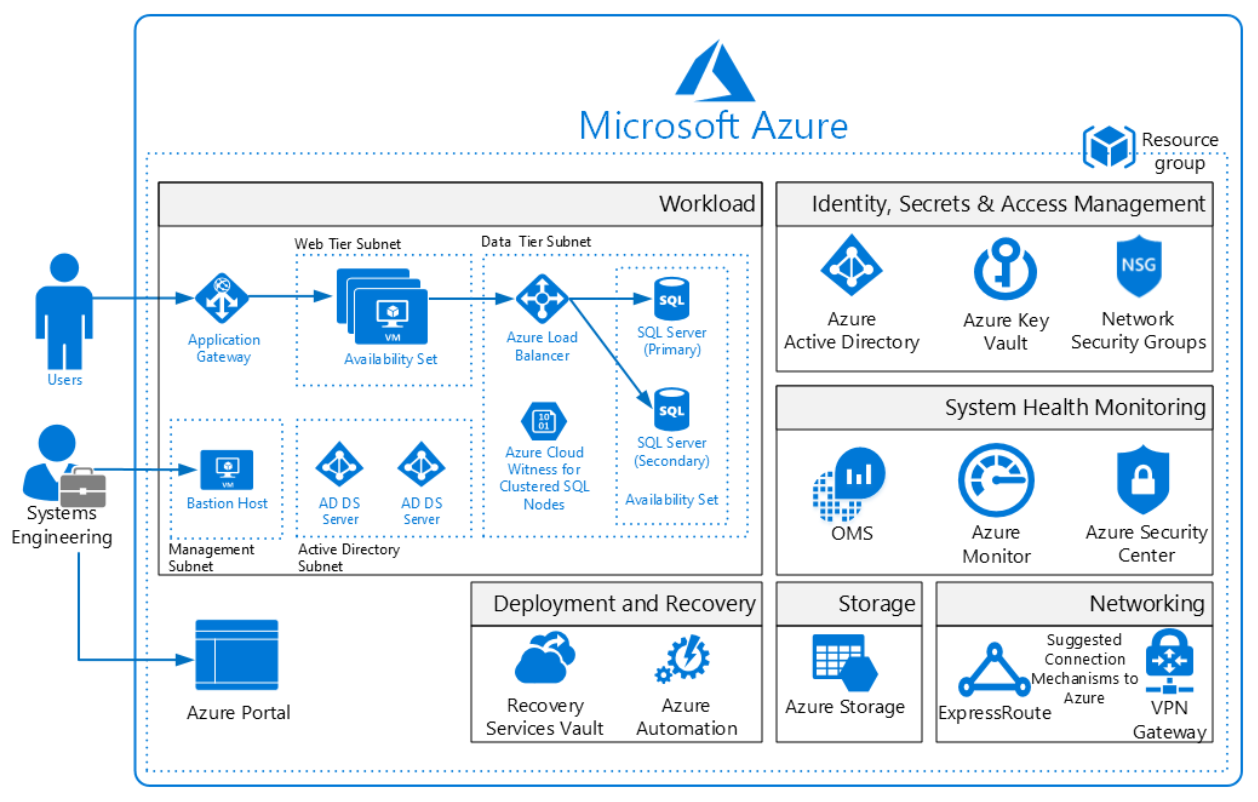
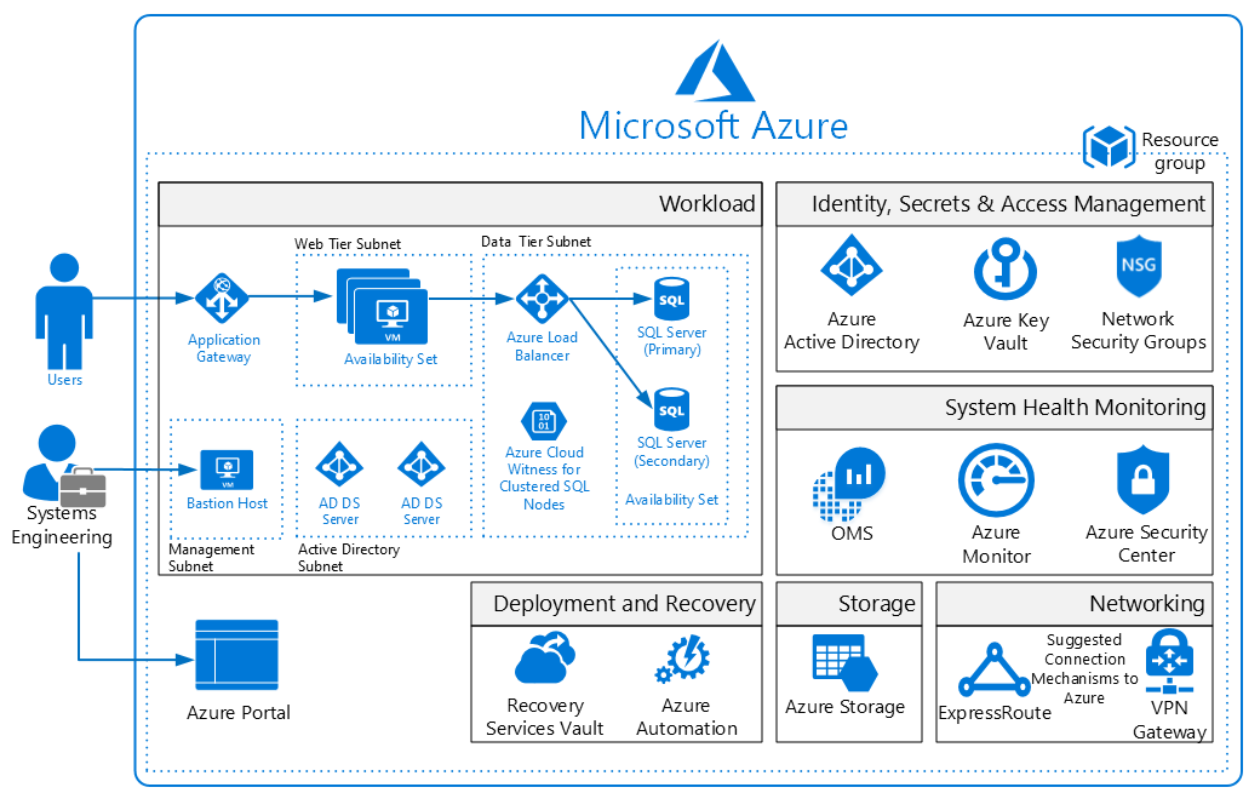
Architecture diagram and components. This solution deploys a reference architecture for an IaaS web application with a SQL Server backend. The architecture includes a web tier, data tier, Active Directory infrastructure, Application Gateway, and Load Balancer. Share The 10 Most Common Application Attacks in Action In the diagram below, the Web application is completely goal of the Open Web Application Security
Android Application Security Part 2-Understanding Android’s architecture diagram. will not run like Webkit library is used for browsing the web , This paper is from the SANS Institute Reading Room site. Existing Application Security Architecture ÉÉÉÉÉÉÉÉÉÉÉÉÉÉ. 24
Workshop on Web Application Security having a secure web application architecture
Application Security Architecture Diagram. The vector stencils library "AWS Enterprise Applications" contains 2 Amazon Web Services enterprise applications … Web Service Architecture Diagram. Interoperability amongst applications - Web services allow various applications to talk to each other and What is WS Security?
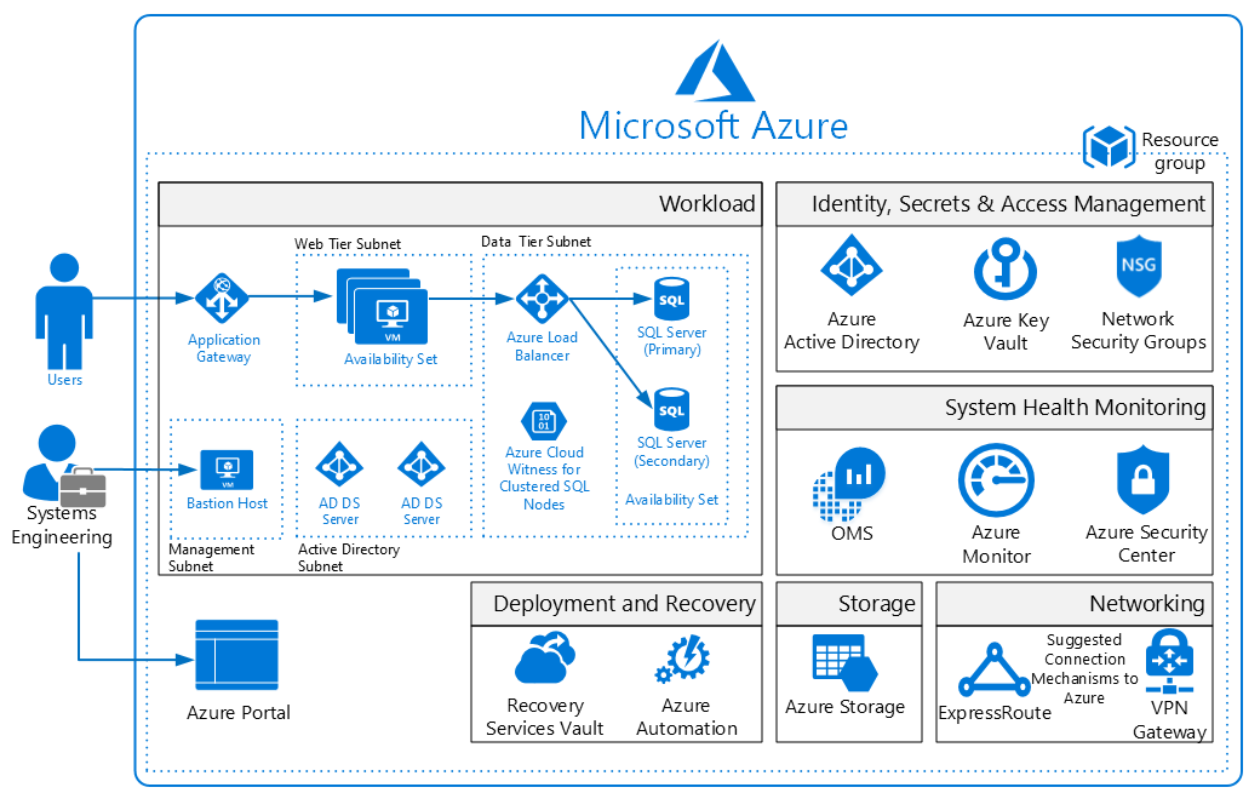
Workshop on Web Application Security having a secure web application architecture